Google Cloud and Australian Privacy Principles
Cloud Whitepaper
Table of Contents
Disclaimer
Introduction
1. The Privacy Act and the Australian Privacy Principles
1.1 What is the Privacy Act?
1.2 The Australian Privacy Principles and Google Cloud
2 . Security and Trusted Infrastructure
2.1 Google data centre infrastructure redundancy
2.2 Google data centre security
2.3 Data in transit
2.3.1 Between a customer and Google
2.3.2 Within Google data centres
2.4 Data at rest
3. Data Protection and Privacy
3.1 Identity and authentication
4. Conclusion
3
3
4
4
5
7
7
8
10
10
10
10
13
13
15

| 3
AUSTRALIAN PRIVACY PRINCIPLES
Disclaimer
This paper is for informational purposes only. Google does not intend the information in this
paper to constitute legal advice. Each customer is responsible for independently evaluating its
own particular use of Google services to support its legal compliance obligations.
Introduction
In this paper Google Cloud refers to the Google Cloud Platform and G Suite products. This
paper is intended to help customers of Google Cloud understand Google’s security and
privacy features. Specically, this paper explains how information is stored, processed,
secured, accessed and maintained in Google Cloud.
This paper has four sections:
• Section 1: The Privacy Act and the Australian Privacy Principles
• Section 2: Security and Trusted Infrastructure
This section provides technical information on how Google Cloud can help customers
keep data secure.
• Section 3: Data Protection and Privacy
This section provides technical information on how Google Cloud can help customers
with identity protection and security.
• Section 4: Conclusion
| 4
AUSTRALIAN PRIVACY PRINCIPLES
Section 1: The Privacy Act and the Australian Privacy Principles
Section 1.1: What is the Privacy Act?
The Privacy Act 1988 (Cth) (Privacy Act), which includes the Australian Privacy
Principles (APP), regulates the way organisations and government agencies handle
the personal information as well as the sensitive information of individuals. There are
13 Australian Privacy Principles.
These Australian Privacy Principles give individuals the right to know why their
personal information is being collected, how their personal information will be used,
and to whom their personal information will be disclosed and to have the ability to ask
for access to, or correction of, their personal information. More details on the Privacy
Act can be found on the Australian Information Commissioner’s website. Customers
of cloud computing providers are responsible for ensuring they comply with their
obligations under the Privacy Act, including the Australian Privacy Principles.
1. Open and transparent management of personal information
2. Anonymity and pseudonymity
3. Collection of solicited personal information
4. Dealing with unsolicited personal information
5. Notication of the collection of personal information
6. Use or disclosure of personal information
7. Direct marketing
8. Cross-border disclosure of personal information
9. Adoption, use or disclosure of government related identiers
10. Quality of personal information
11. Security of personal information
12. Access to personal information
13. Correction of personal information
Personal information management
Data collection
Use and disclosure of data
Data storage, process & management
Identity and authentications
Australian Privacy Principles
| 5
AUSTRALIAN PRIVACY PRINCIPLES
Section 1.2: The Australian Privacy Principles and Google Cloud
Google undergoes several independent third-party audits on a regular basis. These
audits verify the security, privacy and compliance controls present in Google data
centres, its infrastructure and its operations.
Google Cloud Platform is an IaaS/PaaS/SaaS public cloud-based offering from Google.
Google Cloud Platform has annual audits for the following standards:
• SSAE 16 / ISAE 3402 Type II:
SOC 1
SOC 2
SOC 3 public audit report
• ISO 27001 is one of the most widely recognised, internationally
accepted independent security standards. Google has earned
ISO 27001 certication for the systems, applications, people,
technology, processes and data centres serving Google Cloud
Platform. View Google Cloud Platform ISO 27001 Certicate.
Google has also earned the ISO 27001 certication for Google’s
shared Common Infrastructure. View the Common Infrastructure
ISO 27001 Certicate.
• ISO 27017, Cloud Security, is an international standard of practice
for information security controls based on ISO/IEC 27002
specically for cloud services. View the Google Cloud Platform
ISO 27017 Certicate.
• ISO 27018, Cloud Privacy, is an international standard of practice for
protection of personally identiable information (PII) in public cloud
services. View the Google Cloud Platform ISO 27018 Certicate.
| 6
AUSTRALIAN PRIVACY PRINCIPLES
G Suite is an SaaS public cloud-based offering from Google. G Suite is a set of intelligent apps
including Gmail, Docs, Drive, Calendar, G+, Sites and Hangouts. Google designed G Suite to
meet stringent privacy and security standards based on industry best practices. G Suite has
annual audits for the following standards:
• SSAE 16 / ISAE 3402 Type II:
SOC 1
SOC 2
SOC 3 public audit report
• ISO 27001 is one of the most widely recognised, internationally
accepted independent security standards. Google has earned
ISO 27001 certication for the systems, technology, processes
and data centres that run G Suite. View the G Suite ISO 27001
Certicate.
• ISO 27017, Cloud Security, is an international standard of
practice for information security controls based on ISO/IEC
27002 specically for cloud services. View the G Suite ISO 27017
Certicate.
• ISO 27018, Cloud Privacy, is an international standard of practice
for protection of personally identiable information (PII) in public
cloud services. View the G Suite ISO 27018 Certicate.
For more information on Google certications, audits, and
assessments, see the Google Cloud Platform and G Suite
security websites.

| 7
AUSTRALIAN PRIVACY PRINCIPLES
Section 2: Security and Trusted Infrastructure
Google maintains geographically distributed data centres. Google
stores all production data in physically secure data centres.
Section 2.1: Google data centre infrastructure redundancy
Google Cloud Platform services are available in locations across the
Americas, Europe and Asia. These locations are divided into regions
and zones. A full list of Google Cloud Platform regions can be found on
Cloud Locations Map.
Certain Cloud Platform resources are hosted in multiple regions
globally, while other resources, including Cloud Compute Engine Virtual
Machine Instances, persistent disks, Cloud Storage buckets, Cloud App
Engine applications, Cloud Bigtable, Cloud Dataproc, Cloud BigQuery
datasets and Cloud VPN can be created and deployed within specic
geographic regions.
Customers can take advantage of Google Cloud infrastructure by
replicating data within selected geographic regions for redundancy and
availability or by choosing a specic geographic region based on latency
considerations. For more information on data locality for Google Cloud
Platform services, see Geographic management of data and Google
Cloud Platform Service Level Agreements.
Additionally, service-interrupting events can happen at any time. The
network could have an outage; the customer’s latest application push
might introduce a critical bug; or in rare cases, the customer might
even have to contend with a natural disaster. When things go awry, it’s
important to have a robust, targeted and well-tested disaster recovery
plan. Google Cloud Platform provides many of the facilities customers
need to implement such a plan, such as redundancy, scalability,
compliance and security. The Disaster Recovery Cookbook provides
some scenarios to show how Google Cloud Platform can help.
In G Suite, Google designed the platform components to be highly
redundant. This redundancy applies to Google server design, how
Google stores data, network and Internet connectivity and the software
services themselves. This ‘redundancy of everything’ model includes the

| 8
AUSTRALIAN PRIVACY PRINCIPLES
handling of errors by design and creates a solution that is not dependant
on a single server, data centre or network connection. Google’s data
centres are geographically distributed to minimise the effects of regional
disruptions such as natural disasters and local outages. In the event of
hardware, software or network failure, data is automatically shifted from
one facility to another ensuring that G Suite customers can continue
working in most cases without interruption. Customers with global
workforces can collaborate on documents, video conferencing and more
without additional conguration or expense. Global teams share a high
performance and low latency experience as they work together on a
single global network.
Section 2.2: Google data centre security
Google’s data centres employ an electronic card key and biometric access
control system that is linked to a system alarm. The access control
system monitors and records each individual’s electronic card key and
when they access perimeter doors, shipping and receiving, and other
critical areas.
Google’s data centres maintain an on-site security operation responsible for
all physical data centre security functions 24 hours a day, 7 days a week.
The on-site security operation personnel monitor closed-circuit TV (CCTV)
cameras and all alarm systems. On-site security operation personnel
perform internal and external patrols of the data centre regularly.
Google maintains formal procedures for allowing physical access to
the data centres. The data centres are housed in facilities that require
electronic card key access, with alarms that are linked to the on-site
Security Operations. All entrants to the data centre are required to
identify themselves as well as show proof of identity to on-site security
operations. Only authorised employees, contractors and visitors are
allowed entry to the data centres. Only authorised employees and
contractors are permitted to request electronic card key access to these
facilities. Access to a Google data centre’s secure floor, where Google’s
production servers are housed, is controlled via a security corridor that
implements multi-factor access control using security badges and
biometrics. Only approved individuals with specic roles may enter. More
information on Google data centre access and site controls can be found

| 9
AUSTRALIAN PRIVACY PRINCIPLES
on the Google Cloud Platform Data Processing and Security Terms,
Appendix 2: Security Measures and G Suite Data Processing Amendment,
Appendix 2: Security Measures.
Google data centres have been designed to be robust and fault-tolerant in
the following ways:
Power: To support Google’s continuous 24 hours-a-day, seven-days-a-
week operations, a Google data centre’s electrical power systems are
designed to be redundant. A primary and emergency power source,
each with equal capacity, is provided for every critical component in
the data centre. Upon failure of the primary electrical power source,
an uninterruptible power supply (UPS) provides power until the backup
generators can take over. The diesel-engine backup generators are
capable of providing enough emergency electrical power to run the
data centre at full capacity. Examples of events that can cause failures
include utility brownouts, blackouts, over-voltage, under-voltage or out-of-
tolerance frequency conditions.
Climate and temperature: Air cooling is required to maintain a constant
operating temperature for servers and other computing hardware. Cooling
prevents overheating and reduces the possibility of service outage.
Computer-room air conditioning units are powered by both primary and
emergency electrical systems. For more information on cooling control,
see Google data centre temperature control efciency.
Fire detection and suppression: Automatic re detection and suppression
equipment helps prevent damage to computing hardware. The re
detection systems utilise heat, re and smoke detectors located in the data
centre ceilings and underneath the raised floor. In the event of re or smoke,
the detection system triggers audible and visible alarms in the affected
zone, at the security operations console and at the remote monitoring desk.
In addition to automatic re suppression systems, manually operated re
extinguishers are also located throughout the data centre facilities. Google
data centre technicians receive training on re prevention and incipient re
extinguishment, including the use of re extinguishers.
For more information about the Google data centre infrastructure, see
Data Processing and Security Terms, Appendix 2: Security Measures.

| 10
AUSTRALIAN PRIVACY PRINCIPLES
Section 2.3: Data in transit
Google supports various encryption protocols and ciphers to protect data in transit
between the customer and Google. It is the customer’s responsibility to use a secure
browser that supports the latest encryption and security updates. This ensures that
machines connecting to Google Cloud are congured to use appropriate encryption
for Google-to-customer communications.
Data in transit includes data traveling between the customer and Google, and within
Google’s infrastructure. The sections below provide more details on Google’s network
protection and encryption measures for each kind of data in transit.
Section 2.3.1: Between a customer and Google
When a user sends a request to Google, Google secures the data in transit with
authentication, integrity and encryption by using the HTTPS protocol with a
certicate from a public certicate authority. Since 2011, Google has been using
forward secrecy in its transport layer security (TLS) implementation. Forward
secrecy makes sure the key that protects a connection is not persisted, so an
attacker who intercepts and reads one message cannot read previous messages.
The list of Google-supported encryption protocols and ciphers may change
from time to time. For more information on the cryptographic library, see the
BoringSSL library that Google maintains.
Section 2.3.2: Within Google data centres
Remote Procedure Calls (RPC) within Google data centres are cryptographically
authenticated. Jobs in Google’s data centres authenticate RPCs to each other,
and furthermore the infrastructure automatically encrypts all infrastructure RPC
trafc which goes over the WAN between data centres, without requiring any
explicit conguration from the service.
Section 2.4: Data at rest
Google Cloud encrypts customer content stored at rest, without any action required
from the customer, using one or more encryption mechanisms. Data at rest is
encrypted at the storage level using either AES256 or AES128.

| 11
AUSTRALIAN PRIVACY PRINCIPLES
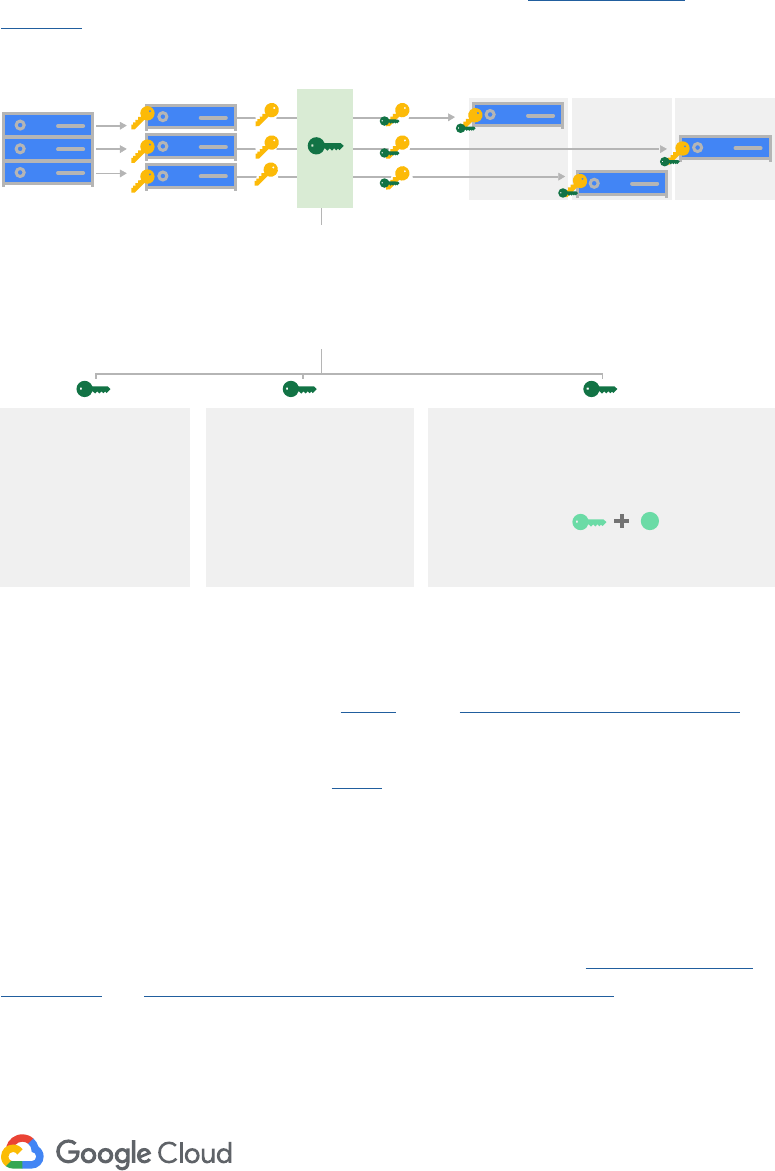
To understand how specically Google Cloud Storage encryption works, it’s important
to understand how Google stores customer data. The diagram below shows how
Google protects data at rest using encryption. The encryption process begins when
data is uploaded to Google Cloud by a customer. Data is broken into suble chunks
for storage; each chunk can be up to several GB in size. Each chunk is encrypted at
the storage level with a unique data encryption key, which uses AES128 or higher:
two chunks will not have the same encryption key, even if they are part of the same
Google Cloud Storage object, owned by the same customer or stored on the same
Google machine. If a chunk of data is updated, it is encrypted with a new key, rather
than by reusing the existing key.
Due to the high volume of keys at Google, and the need for low latency and high
availability, data encryption keys are stored near the data that they encrypt. The data
encryption keys are themselves encrypted with a key encryption key which uses
AES128 or higher.
Access control lists (ACLs) in Google’s internal Key Management Service ensure that
each chunk can be decrypted only by Google services operating under authorised
roles, which are granted access at that point in time. This prevents access to the
data without authorisation, bolstering both data security and privacy. If a malicious
individual wanted to access customer data, that individual would need to: (1) know
and be able to access all storage chunks corresponding to the data they want, (2)
know and be able to access the encryption keys corresponding to the chunks, and (3)
have authorised role credentials.
Data is uploaded
to Google
Data is chunked and each
chunk is encrypted with
its own key
Chunks are distributed across
Google’s storage infrastructure
| 12
AUSTRALIAN PRIVACY PRINCIPLES
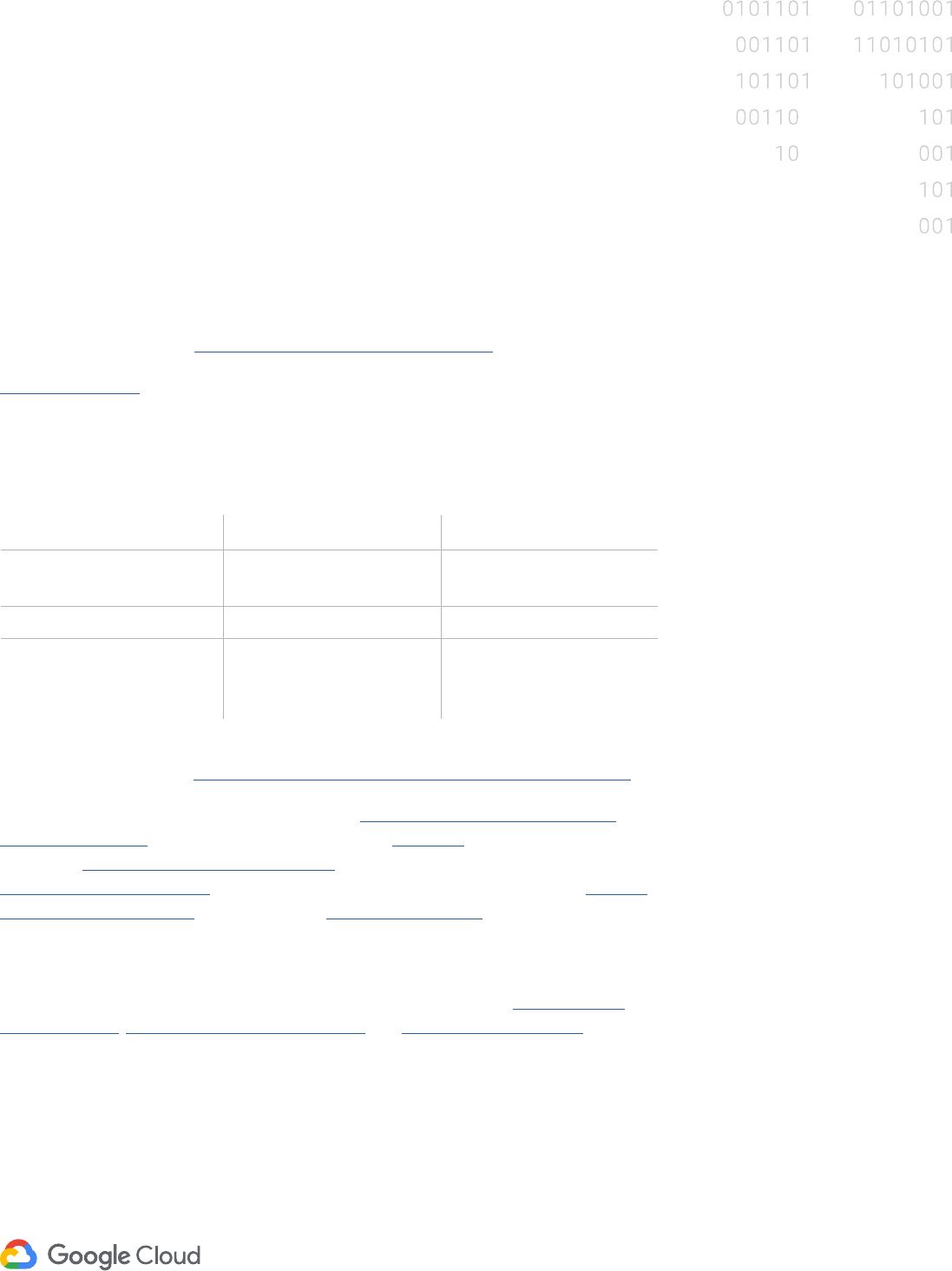
In Google Cloud Platform, customers can choose one of the key management
solutions as shown in the diagram below to manage the key encryption keys that
protect the data encryption keys that protect their data.
• Default Google encryption: Key encryption keys are stored in Google’s internal Key
Management Service.
• Customer-managed encryption keys (CMEK) using Cloud Key Management Service
(KMS): Key encryption keys are stored in Cloud KMS.
• Customer-supplied encryption keys (CSEK), available in Google Compute Engine and
Google Cloud Storage services: Key encryption keys are provided by the customer
as part of every API call.
In addition, customers can encrypt the data themselves before importing it into
Google Cloud Platform services.
For more information on encryption and key management, see the G Suite Encryption
Whitepaper and Google Cloud Platform Encryption at Rest Whitepaper.
Data is chunked
and each chunk is
encrypted with its
own key
Data is
uploaded to
Google
Data encryption keys
(DEKs) are wrapped
using a key encryption
key (KEK)
Encrypted chunks and
wrapped encryption keys are
distributed across Google’s
storage infrastructure
Default Google
encryption
Customer-supplied
encryption keys (CSEK)
Customer-managed
encryption keys (CMEK)
using Cloud KMS
Key encryption
key retrieved from
Cloud KMS
Key encryption key
retrieved from Google
internal KMS
KEK derived from
CSEK + nonce
Key supplied via
Customer-Supplied
Encryption Key
(CSEK) API
Per-resource
random
cryptographic
nonce
1

| 13
AUSTRALIAN PRIVACY PRINCIPLES
Section 3: Data Protection and Privacy
ISO 27018, Cloud Privacy, is an international standard of practice for protection of
personally identiable information (PII) in public cloud services. For more information
on the complete list of services that are ISO 27018 certied, see Google Cloud
Platform and G Suite security websites.
Google offers its customers a detailed G Suite Data Processing Amendment and
Google Cloud Platform Data Processing and Security Terms that describe its
commitment to protecting customer data.
Section 3.1: Identity and authentication
Google Cloud Platform and G Suite use Google Accounts for authentication and
access management. Google recommends using fully managed corporate Google
accounts for increased visibility, auditing and control over access to Cloud Platform
resources.
Cloud Identity provides free, managed Google Accounts you can use with Google
services including Cloud Platform. Using Cloud Identity accounts for each of your users,
you can manage all users across your entire domain from the Google Admin console.
If you’re a G Suite administrator, you can manage all of your users and settings through
the G Suite Admin Console. By default, all new users are assigned a G Suite license. If
you have a subset of developers who don’t require G Suite licenses, you can add Cloud
Identity accounts instead. For more information, see Get started with Cloud Identity.
The customer is responsible for managing all aspects of access control
(authentications) for the customer’s users of Google Cloud, and can take advantage
of rich authentication features including single sign-on (SSO), OAuth and two-factor
verication to protect their Google Accounts.
Single sign-on (SSO): Google supports SAML 2.0-based SSO, which provides seamless
SSO against Cloud Platform Console, web- and command-line-based SSH, and OAuth
authorisation prompts. Cloud Platform’s command-line interface tools, such as
gcloud, gsutil, and bq, use SAML 2.0-based SSO for browser-based authentication as
well. For information about setting up Google SSO, see Set up Single Sign-On for G
Suite accounts. This guide applies to both Cloud Platform and G Suite, because both
products share a common directory, authentication and SSO infrastructure.
| 14
AUSTRALIAN PRIVACY PRINCIPLES
OAuth: Google APIs use OAuth 2.0 protocol for authentication and authorisation to
determine the identity of a user and what permissions an authenticated user has on
a set of specic resources. Google supports common OAuth 2.0 scenarios such as
those for web server, installed and client-side applications. For information about
setting up OAuth 2.0, see Using OAuth 2.0 to access Google APIs.
2-Step Verication: A combination of a Google password and a credential, using
Google 2-Step Verication adds an extra layer of security to a customer account by
requiring the user to enter a verication code or use a physical security key in addition
to their username and password when signing into their account. Google provides
three simple ways to implement 2-Step Verication.
Verication Method Software or Hardware Requirements
Text message Software Cellular service and a
powered mobile device
Google Authenticator Software Powered mobile device
Security Keys Hardware Google Chrome desktop
browser (version 40+), iOS,
Android
More information on how to set up the security keys on a Google Cloud Platform
account can be found on Securing your Cloud Platform Account with Security Keys.
In addition, the Google Cloud Platform product, Google Cloud Identity and Access
Management (IAM) can help customers to manage individual access permissions
for certain Google Cloud Platform resources. Customer can assign individuals to a
group and role membership by conguring their application via Google Cloud Identity
and Access Management (IAM) policies or Access Control Lists (ACLs). This access
management can help the customer to address the privacy of the individual’s data
and ensure that each individual only has access to their own data.
Google also provides a set of logging and monitoring tools, such as G Suite Admin
Console Report, Google Cloud Platform Console and Google Cloud audit logs, that
make it possible to collect and analyse request logs and monitor user activities.

| 15
AUSTRALIAN PRIVACY PRINCIPLES
Section 4: Conclusion
This document describes how information is stored, processed, maintained, secured
and accessed in Google Cloud using Google Cloud products. This information can
help customers when considering whether Google’s products are suitable for them. In
particular it explains how Google approaches security and privacy. A more in-depth
understanding of how Google Cloud products work can be found in references cited
within this document.
Google Cloud security
For general information on Google security and encryption of data at rest, see the
Google Cloud whitepapers website.
Google Cloud Platform compliance
For information on Google Cloud Platform compliance and compliance certications,
see the Compliance section of the Google Cloud Platform website.
G Suite compliance
For information on G Suite compliance and compliance certications, see the
Compliance section of the G Suite website.
